A cyber security incident response plan checklist is the best way to ensure that no one misses any incident particulars. Determining the scope of a cyber data breach incident requires that your team cover all the basics and components of the framework constructed by the National Institute of Standards and Technology. This guide will review the NIST framework, the basis of the checklist we have for you. The list will help guide your team through the appropriate steps to manage incidents.
Our Cyber Security Incident Response Plan Checklist helps organizations to create robust strategies for dealing with data breach scenarios and is a vital component in any preventative methodology.
Let’s start by looking at the key components that create the incident response plan checklist together. Then we’ll review the best practices and offer vital tips to help you and your team prevent and mitigate incident situations with appropriate and professional responses.
Included In Cyber Security The Incident Response Plan Checklist
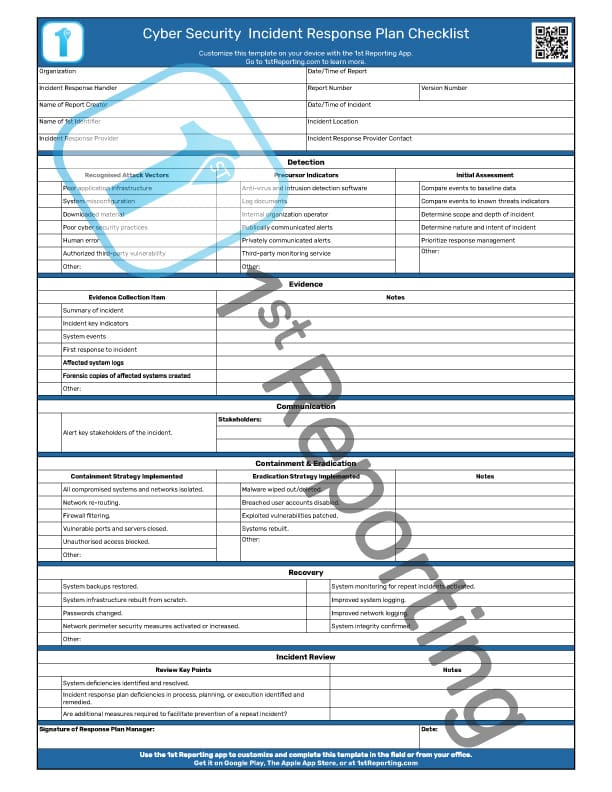
The Incident Response Plan Checklist has seven sections for your convenience. We’ve ordered the segments to help your team proceed in the correct order. Let’s review each section now, and feel free to bookmark this page so you can use it to help train your team on the checklist use.
Administrative Information
Ensuring the appropriate documentation of an event occurrence is paramount. Furthermore, it’s wise to assign a report number and include other pertinent information for future data retrieval. The administrative section at the top of the Incident Response Plan Checklist ensures that this data is appropriately captured and recorded for future reference.
Incident Detection
Upon initial incident detection, you and your team spring into action. The incident detection segment of the checklist provides you with the correct queries to ask to convey how the threat detection process played out.
Incident Evidence Gathering
Gathering evidence of a cybersecurity breach is critical to establishing the details of the incident. This segment of the Incident Response Plan Checklist provides your team with a place to detail the evidence and guides them through the right questions to ask. Furthermore, we’ve provided a sizeable free-writing text area to document and record observations and evidence information.
Incident Communication
Following any cybersecurity incident, the proper stakeholders must receive communications regarding the incident. Essential personnel must implement incident mitigation protocol, so contact must occur immediately following an incident.
Threat Containment and Eradication
Post identification, a threat must become neutralized in one way or another. Some threats will require containment, and others will require complete eradication. The nature and extent of the danger will determine these particulars. However, our checklist works for either scenario, and all your team needs to do is complete the checklist accordingly.
Incident Recovery
Cybersecurity incidents, and any other type, require that your operations recover and continue business as usual. However, it is critical to detail certain aspects of the incident recovery process. Similarly, there are specific steps that are best answered in consecutive order. Therefore, utilizing the incident recovery portion of the checklist is a critical step to successful operations.
Incident Review
After any incident scenario, it would be best if you and your team reviewed it. Here’s where having an incident response checklist is convenient. Memory lapses and fades, and we, as humans, tend to remember things jaded by our personal biases. Therefore, the utilization of a standardized incident reporting system is paramount.
Following your incident, the review process enables an introspective look at strategies to foster positive change. After all, prevention only occurs when we know what to prevent. Therefore the incident review is as indispensable as the initial response to a threat in the first place.
How To Use The Incident Response Plan Checklist

Using the Incident Response Plan Checklist is relatively straightforward. Begin by downloading and printing copies of the checklist. Next, dispense them to your teams and provide instructions on how you want incidents mitigated and reported.
The entire concept of managing an incident with the use of an incident response plan checklist is to do four primary things:
- Halt an attack in progress
- Minimize damage and adverse effects of the incident
- Recover as much as possible.
- Prevent further recurrences of the threat.
Another way to use our incident response plan checklist is to use the digital version in our reporting app, 1st Reporting. Using the digital version is easy; just follow the following steps.
- Install the app on your smartphone or tablet and get your team to do the same.
- Log in to the app and create your account.
- Open our Incident Response (IR) Plan Checklist and customize it to fit your brand using our form builder and customizer.
- Please set up your team using the same IR plan checklist in the app.
- If you want, you can also set up custom notifications, so the right person gets a notification when someone in the team completes an IR form.
Tips For Better Incident Documentation and Management

Documentation of incidents and inspections is a critical requirement, not only for regulatory compliance but, more importantly, for the pursuit of a safer work environment. Whether you work in HR, management, or another role, you can appreciate the importance of a safe workplace. So, how do we further improve workplace safety documentation? We’ve got a few ideas.
The best way to manage incident and inspection documentation processes is by utilizing a robust emergency response plan included in your health and safety manual. Let’s look at some of the best industry tips to help us with this process.
Prepare for every possibility with good planning.
Good incident prevention starts with robust planning. Understanding your systems architecture, weaknesses, and vulnerabilities allows you to compensate by planning measures that suit your systems setup. It’s worth taking the time to plan and prepare for eventualities that could cause damage to your operations.
This method of managing incident prevention doesn’t have to only apply to cybersecurity and IT infrastructure. In fact, it’s noteworthy to consider that proper preparations are critical no matter what industry you operate in.
Utilize strategic prevention measures.
Following a solid planning phase should lead you to the inevitable conclusion to work on patching and preventing weaknesses and intrusion points. With intelligent planning, we can insert the appropriate network cutoff points and system critical backups to ensure that we can segregate infected systems or networks and rebuild databases with untainted information. You can strategically prevent many threats by designing safeguards into the system infrastructure. The point is to ensure you do two things: a) dedicate enough time and resources to proper preemptive planning and b) build safeguards into systems to help stop threats in their tracks.
Build out standardized policies and include regular and systematic training.
Something that can destroy an organization is a lack of standardization. Although each organization and situation is different, we can create and utilize standardized response procedures. By including these procedures in a particular role’s responsibilities, we can better manage the response to incidents.
Take advantage of modern technology and improve efficiency.
A picture speaks a thousand words. And a file with documented evidence of a cyber attack or other incidents can be the critical information needed. However, a piece of paper can’t upload a file, and your team has better things to do than write out mundane paper reports. That’s why modern technology is more than just a convenience – it’s a literal improvement in the efficiency of operations. Here’s how it can help you:
Look around your office, and you’re bound to notice some paper. If your organization is still writing paper reports, then you likely have your hands full of paperwork. However, modern technology replaces that millennia-old invention with something the world has never seen before.
Enter the 1st Reporting app.
We made our application with your organization and all the paperwork in mind. Let’s take the incident response plan checklist as our example. Sure, it’s great to download and print a copy of our checklist, but don’t you think it’s time to consider saving money? Here are six ways you are losing by using paper reports:
- Ink and paper aren’t cheap.
- Boxes of paper take up valuable real estate.
- Filing cabinets and printers also take up space.
- Printers use electricity and often stay on all day and night.
- Paper reports are only as neat and organized as the handwriting that wrote them.
- Paper reports are easy to damage and even easier to lose.
We are your number-one source for professional checklists and report forms, but with our app, 1st Reporting, you’ll be number one in your industry for efficient reporting. Furthermore, you can manage your team in-house or remotely by taking advantage of the dynamic forms, custom form builder, and notifications. Setting up the system is easy, straightforward, and clear, making it a breeze to implement in place of paper forms and checklists.
Start your free trial today and find out for yourself what a professional reporting platform can do to transform your operations into a streamlined thing of beauty. Not sure? Why not book a demo with one of our team? That way, you can also learn first-hand the level of real support that you should be getting; we strive to be there for you and your team because incident response just can’t wait.